How To – Monitor Split Tunnel Traffic with Catchpoint
When the world transitioned to a remote workspace, one of the things that most of us figured out quickly was that some applications just don’t work well with corporate VPN. Video and voice applications, like Microsoft Teams, are essential to business operations. I wouldn’t want to add another point of failure that I’d need to troubleshoot if I didn’t have to.
One easy way to get around such complexity is to “split tunnel” your traffic. Split tunnel allows you to exclude an application from the VPN. Split tunneling helps conserve bandwidth while still enabling users unfettered access to local resources. It’s a great solution for multiple use cases. For example, people living overseas or people who need access to sensitive data and applications but also have a performance requirement.
In today’s how-to video, we show you how to use Catchpoint to monitor split tunnel traffic.
Impact on Performance And Security
One issue that comes with split tunneling is that when people use endpoint clients and VPNs to define their business perimeter, corporate IT starts to lose visibility. Employee activity on a split-tunneled device is inherently riskier than pushing traffic through an encrypted VPN. This doesn’t just include visiting forbidden sites, less secure networks or security practices add to the network vulnerability.
If you have an application that needs to be split-tunneled, you’ll be able to identify and monitor it through Catchpoint. Thanks to our robust Endpoint Client and Network Insights module, we can pull live data from your employee’s network and identify whether or not traffic is being pushed through your VPN or not. This is effective whether you’re checking the performance of a video application, or making sure people are using the correct protocol when accessing something like financial data.
We’re going to look at an endpoint Catchpoint is currently monitoring, see what data Catchpoint pulls to help provide better endpoint visibility, and then track a specific application and determine whether or not it’s being split-tunneled.

In the image above, we can see a smartboard displaying data from my Catchpoint endpoint client. There is a lot of data relevant to my device from the end-user perspective. Specifically, it indicates that the device has a decent network and application score, but that I’m also running into issues on the endpoint side. Here, we can interpret ‘endpoint’ to mean “network and device elements local to the user.”
Using our Network Insights feature, I can analyze my outbound connections (Fig 1).
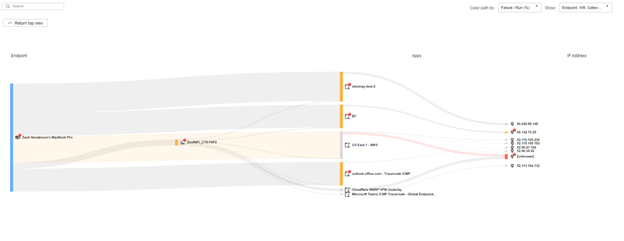
Fig 1
Let’s analyze the network path, we see that a lot of the traffic is actually being pushed through VPN (Fig 2).

Fig 2
Let’s go further and dig into data from Microsoft Teams. We see that it’s not passing through the VPN. The traffic is instead going out directly to the Teams IP address. This is important information for me and my IT team in case people start reporting issues with the application.
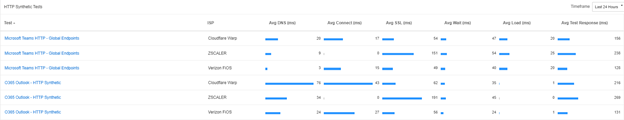
Fig 3
In the dashboard above (Fig 3), we take a step further to determine how our applications are performing on various clients. You can see that I have Cloudflare WARP and Zscaler installed on the same device. The Microsoft Teams test can be used to evaluate application performance based on live user data. Each column indicates how Catchpoint can identify endpoint client providers and distinguish between them for evaluation purposes.
And with that, you now know how to monitor split-tunneled traffic with Catchpoint. Thanks for reading!



